Physical Unclonable Functions
Einzigartige Identitäten und kryptographische Schlüssel aus Hardwareeigenschaften
Kontakt: Michael Pehl (Gruppenleitung), Christoph Frisch, Jonas Ruchti, Tim Music
Eine Physical Unlonable Function (PUF) wertet Fertigungsschwankungen in einem Chip aus und erzeugt daraus ein individuelles Signal, das ähnlich wie ein eingescannter Fingerabdruck von Chip zu Chip stark und von Messung zu Messung leicht variiert.
Eine PUF erzeugt also ein verrauschtes Geheimnis reproduzierbar zur Laufzeit. Dieses Geheimnis kann entweder dazu genutzt werden, den Chip zu authentifizieren, oder es steht nach Entfernen des Rauschens als kryptografischer Schlüssel zur Verfügung.
Durch PUFs erhalten auch Systeme ohne sichere Schlüsselspeicher Zugang zu sicheren kryptografischen Schlüsseln.
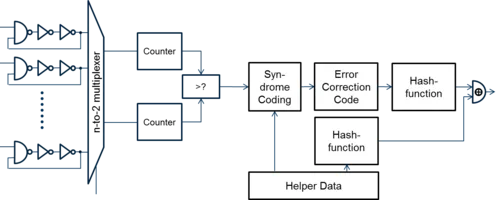
Forschungsthemen
- Neue PUF Primitive und Architekturen insbesonder auch Memristor-basierte PUFs
- Simulation und Entwurf von PUFs
- Schlüsselextraktion und Fehlerkorrektur für PUFs
- Integration von PUFs in eingebettete Systeme
- Protokolle für PUFs
- Angriffe auf PUFs
- Fingerprinting
Lehre zur Forschung
Seit 2018 wird zu diesem Forschungsgebiet die Vorlesung Physical Unclonable Functions angeboten.
Unser Tool zur Evaluierung von PUFs kann unter https://gitlab.lrz.de/tueisec/PQAS heruntergeladen werden.
Aktuelle Projekte in diesem Bereich
- VE-FIDES (Knowhow-Schutz und Identifizierbarkeit von Elektronikkomponenten für vertrauenswürdige Produktionsketten)
Unser Beitrag: Verwendung von PUFs zur Absicherung der Lieferkette.
[Link zum Projekt] - APRIORI (Resilienz gegen Fehlerinjektionsangriffe für verbesserten Datenschutz von IoT-Endgeräten):
Unser Beitrag: Fehlerangriffe auf PUFs und Schutzmechanismen; Projektleitung
[Link zum Projekt] - 6G Zukunftslabor Bayern – 6G Future Lab Bavaria:
Verwendung von PUFs in 6G Netzwerken.
[Link zum Projekt]
Ausgewählte Veröffentlichungen
Lars Tebelmann, Ulrich Kühne, Jean-Luc Danger, and Michael Pehl, Analysis and Protection of the Two-Metric Helper Data Scheme, International Workshop on Constructive Side-Channel Analysis and Secure Design. Springer, Cham, 2021. [Download from eprint]
Emanuele Strieder, Christoph Frisch, and Michael Pehl, Machine Learning of Physical Unclonable Functions using Helper Data: Revealing a Pitfall in the Fuzzy Commitment Scheme, IACR Transactions on Cryptographic Hardware and Embedded Systems, 2021(2), 1-36. https://doi.org/10.46586/tches.v2021.i2.1-36i
Lars Tebelmann, Jean-Luc Danger, and Michael Pehl. Self-secured PUF: protecting the loop PUF by masking, International Workshop on Constructive Side-Channel Analysis and Secure Design. Springer, Cham, 2020. [Download from eprint]
Lars Tebelmann, Michael Pehl, and Vincent Immler. Side-channel analysis of the TERO PUF, International Workshop on Constructive Side-Channel Analysis and Secure Design. Springer, Cham, 2019. [Download from eprint]
Florian Wilde, Berndt Gammel, and Michael Pehl, Spatial Correlation Analysis on Physical Unclonable Functions, IEEE Transactions on Information Forensics and Security (Volume: 13 Issue: 6), 2018, pages: 1468-1480; Tool published with it
Lars Tebelmann, Michael Pehl, and Georg Sigl, EM side-channel analysis of BCH-based error correction for PUF-based key generation, Proceedings of the 2017 Workshop on Attacks and Solutions in Hardware Security. 2017.
Michael Pehl, Matthias Hiller, and Georg Sigl, Secret Key Generation for Physical Unclonable Functions – Secret Key Generation and Authentication, In: Information Theoretic Security and Privacy of Information Systems, Cambridge, 2017
Florian Wilde, Large Scale Characterization of SRAM on Infineon XMC Microcontrollers as PUF. 4th Workshop on Cryptography and Security in Computing Systems (CS2 2017) HIPEAC17 , 2017 Public PUF dataset published with it
Matthias Hiller, Meng-Day (Mandel) Yu, and Sigl, Georg, Cherry-Picking Reliable PUF Bits with Differential Sequence Coding, IEEE Transactions on Information Forensics and Security (Volume: 11 Issue: 9), 2016, pages: 2065-2076
Matthias Hiller, Meng-Day (Mandel) Yu, and Michael Pehl, Systematic Low Leakage Coding for Physical Unclonable Functions, ACM Symposium on Information, Computer and Communications Security (ASIACCS), 2015
Florian Wilde, Matthias Hiller, and Michael Pehl, Statistic-based security analysis of ring oscillator PUFs, 2014 International Symposium on Integrated Circuits (ISIC). IEEE, 2014.
Matthias Hiller, Dominik Merli, Frederic Stumpf, and Georg Sigl, Complementary IBS: Application Specific Error Correction for PUFs, IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), pp. 1-6, June 2012.