- Transform to XML failed
- CC:XSLT processing: Transformation failed.
Physical Unclonable Functions
Unique identities and cryptographic keys form hardware intrinsic features
Contact: Michael Pehl (group leader), Christoph Frisch, Jonas Ruchti, Tim Music
Physical Unclonable Functions (PUFs) evaluate manufacturing variations in integrated circuits and generate an individual response for each device. This response significantly varies from chip to chip but only slightly from measurement to measurement.
Some PUF types can be configured with challenges and give unpredictable responses based on the applied challenge. These PUFs can be used for secure authentication.
Other PUFs show one unique pattern similar to a biometric fingerprint. These patterns are the foundation for secure key generation with PUFs.
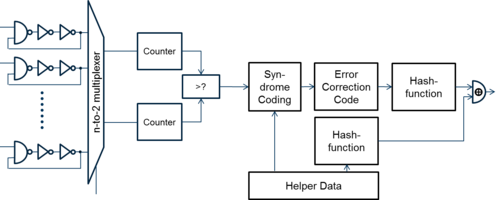
Syndrome coding creates helper data that enables on-chip error correction for secret keys. In addition, error-correcting codes are used to correct remaining errors. Hash-functions can compress generated secrets to smaller keys or prevent helper data manipulation attacks. Therefore, PUFs provide secure cryptographic keys for devices without secure key storage.
Research Topic
- New PUF primitives and architectures (in particular also Memristor-based PUFs)
- Statistical analysis of PUF data
- Design of new syndrome coding schemes
- Key extraction and error correction for PUFs
- Integration of PUFs into embedded systems
- Protocols for PUFs
- Attacks on PUFs
- Fingerprinting
Teaching in this Research Area
Since 2018, the lecture Physical Unclonable Functions is provided for this research field.
Our tool for PUF evaluation can be downloaded from https://gitlab.lrz.de/tueisec/PQAS.
Open Theses Topics and Student Positions in this Field
Current Projects in this Field
- VE-FIDES (IP Protection and Indentification of Electronic Devices for Trustworthy Supply Chains)
Our contribution: Verwendung von PUFs zur Absicherung der Lieferkette.
[Link to project] - APRIORI (Advanced Privacy of IoT Devices through Robust Hardware Implementations):
Our contribution: Fault Attacks on PUFs and Countermeasures; Project Lead
[Link to project] - 6G Zukunftslabor Bayern – 6G Future Lab Bavaria:
Our contribution: Usage of PUFs in 6G Networks.
[Link to project]
Selected Publications
Lars Tebelmann, Ulrich Kühne, Jean-Luc Danger, and Michael Pehl, Analysis and Protection of the Two-Metric Helper Data Scheme, International Workshop on Constructive Side-Channel Analysis and Secure Design. Springer, Cham, 2021. [Download from eprint]
Emanuele Strieder, Christoph Frisch, and Michael Pehl, Machine Learning of Physical Unclonable Functions using Helper Data: Revealing a Pitfall in the Fuzzy Commitment Scheme, IACR Transactions on Cryptographic Hardware and Embedded Systems, 2021(2), 1-36. https://doi.org/10.46586/tches.v2021.i2.1-36i
Lars Tebelmann, Jean-Luc Danger, and Michael Pehl. Self-secured PUF: protecting the loop PUF by masking, International Workshop on Constructive Side-Channel Analysis and Secure Design. Springer, Cham, 2020. [Download from eprint]
Lars Tebelmann, Michael Pehl, and Vincent Immler. Side-channel analysis of the TERO PUF, International Workshop on Constructive Side-Channel Analysis and Secure Design. Springer, Cham, 2019. [Download from eprint]
Florian Wilde, Berndt Gammel, and Michael Pehl, Spatial Correlation Analysis on Physical Unclonable Functions, IEEE Transactions on Information Forensics and Security (Volume: 13 Issue: 6), 2018, pages: 1468-1480; Tool published with it
Lars Tebelmann, Michael Pehl, and Georg Sigl, EM side-channel analysis of BCH-based error correction for PUF-based key generation, Proceedings of the 2017 Workshop on Attacks and Solutions in Hardware Security. 2017.
Michael Pehl, Matthias Hiller, and Georg Sigl, Secret Key Generation for Physical Unclonable Functions – Secret Key Generation and Authentication, In: Information Theoretic Security and Privacy of Information Systems, Cambridge, 2017
Florian Wilde, Large Scale Characterization of SRAM on Infineon XMC Microcontrollers as PUF. 4th Workshop on Cryptography and Security in Computing Systems (CS2 2017) HIPEAC17 , 2017 Public PUF dataset published with it
Matthias Hiller, Meng-Day (Mandel) Yu, and Sigl, Georg, Cherry-Picking Reliable PUF Bits with Differential Sequence Coding, IEEE Transactions on Information Forensics and Security (Volume: 11 Issue: 9), 2016, pages: 2065-2076
Matthias Hiller, Meng-Day (Mandel) Yu, and Michael Pehl, Systematic Low Leakage Coding for Physical Unclonable Functions, ACM Symposium on Information, Computer and Communications Security (ASIACCS), 2015
Florian Wilde, Matthias Hiller, and Michael Pehl, Statistic-based security analysis of ring oscillator PUFs, 2014 International Symposium on Integrated Circuits (ISIC). IEEE, 2014.
Matthias Hiller, Dominik Merli, Frederic Stumpf, and Georg Sigl, Complementary IBS: Application Specific Error Correction for PUFs, IEEE International Symposium on Hardware-Oriented Security and Trust (HOST), pp. 1-6, June 2012.