Embedded Systems and Security
Lecturer: Jens Nöpel und Manuel Brosch
| Nummer | 0000005024 |
|---|---|
| Art | Praktikum |
| Umfang | 1 SWS |
| Semester | Sommersemester 2025 |
| Unterrichtssprache | Deutsch |
| Stellung in Studienplänen | Siehe TUMonline |
| Termine | Siehe TUMonline |
-
(Keine Termine gefunden)
Teilnahmekriterien
Lernziele
- Toolchains für eingebettete Systeme zu benutzen
- Zu erläutern, wie Speicher organisiert ist
- Speichertypen in Chips zu klassifizieren
- Den Startvorgang eines Mikrocontrollers wiederzugeben
- 'memory mapped I/O' beschreiben zu können und es zu nutzen
- Übliche Peripheriebausteine aufzuzählen und deren Zweck zu erklären
- Interrupts erklären zu können und sie zu nutzen
- Debugmöglichkeiten für eingebettete Systeme vergleichen zu können und zu nutzen
während der zweite Teil folgende Fähigkeiten umfasst
- Schutzziele aufzählen zu können
- Beispiele für typische Schwachstellen zu geben
- Einige übliche Angriffe anzuwenden
- Angemessene Gegenmaßnahmen auszuwählen
- Kryptographie zu nutzen
- Mittel und Wege zur Separation darzulegen
- MMUs/MPUs erklären zu können und sie zu nutzen
- Seitenkanäle erklären zu können
- Das Konzept von 'trusted computing' darzulegen
Beschreibung
- Speicher in eingebetteten Systemen und dessen Nutzung durch C Compiler
- Typische Peripheriebausteine und deren Nutzung
- Interrupts und Exceptions
- Debugging von eingebetteten Systemen
- Kurzeinführung in Schutzziele und kryptographische Operationen
- Typische Schwachstellen in eingebetteten Systemen
- Übliche Angriffe und Gegenmaßnahmen
- Anmerkung zu Seitenkanälen
- Konzept von Separation und 'trusted computing'
Inhaltliche Voraussetzungen
Grundkenntnisse im Bereich Computerarchitekturen
Lehr- und Lernmethoden
Studien-, Prüfungsleistung
Empfohlene Literatur
Joseph Yiu
Understanding Cryptography
Christoph Paar, Jan Pelzl
Accompanied lecture slides: http://www.crypto-textbook.com
Handbook of Applied Cryptography
Alfred J. Menezes, Paul C. van Oorschot, Scott A. Vanstone
Download from: http://www.cacr.math.uwaterloo.ca/hac/
Security Engineering
Ross Anderson
Download from: https://www.cl.cam.ac.uk/~rja14/book.html
Links
Hinweis und Weitere Informationen
Die Vorlesung wird um ein Praktikum um eine SWS ergänzt.
Wird im Winter- und Sommersemester angeboten.
Programmierübungen auf einem eingebetteten System von Infineon ermöglichen es, die erlernten Inhalte praktisch einzusetzen.
Moodle
Die Folien werden nach der Vorlesung unter Moodle bereitgestellt
Sprache
Englisch (WiSe), Deutsch (SoSe)
Murmelbahn
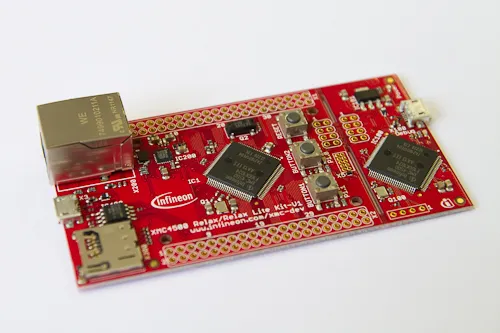
Im Rahmen der Embedded Systems and Security Übung programmieren die Studierenden eine Fernsteuerung auf einem Infineon XMC4500 Relax Lite Board für die Murmelbahn im Video. Bei einer erfolgreichen Authentifizierung können die Studierenden die Bahn von ihrem Board auslösen.
Alternativ kann die Murmelbahn durch das brechen einer 16 Bit Mini RSA Verschlüsselung gestartet werden.
Sie ist erreichbar unter http://10.152.249.7/ (innerhalb des TUM Netzwerks)
Infineon XMC4500 Relax Kit