Embedded Systems and Security
| Lecturer (assistant) | |
|---|---|
| Number | 0000004160 |
| Type | lecture |
| Duration | 2 SWS |
| Term | Wintersemester 2025/26 |
| Language of instruction | English |
| Position within curricula | See TUMonline |
| Dates | See TUMonline |
- 14.10.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 16.10.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 21.10.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 23.10.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 28.10.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 30.10.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 03.11.2025 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 04.11.2025 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 04.11.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 06.11.2025 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 06.11.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 07.11.2025 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 07.11.2025 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 10.11.2025 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 11.11.2025 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 11.11.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 13.11.2025 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 13.11.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 14.11.2025 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 14.11.2025 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 17.11.2025 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 18.11.2025 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 18.11.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 20.11.2025 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 20.11.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 25.11.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 27.11.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 28.11.2025 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 28.11.2025 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 01.12.2025 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 02.12.2025 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 02.12.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 04.12.2025 10:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 05.12.2025 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 05.12.2025 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 08.12.2025 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 09.12.2025 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 09.12.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 11.12.2025 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 11.12.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 12.12.2025 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 12.12.2025 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 15.12.2025 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 16.12.2025 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 16.12.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 18.12.2025 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 18.12.2025 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 19.12.2025 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 23.12.2025 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 08.01.2026 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 08.01.2026 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 09.01.2026 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 09.01.2026 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 12.01.2026 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 13.01.2026 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 13.01.2026 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 15.01.2026 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 15.01.2026 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 16.01.2026 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 16.01.2026 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 19.01.2026 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 20.01.2026 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 20.01.2026 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 22.01.2026 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 22.01.2026 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 23.01.2026 14:00-16:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 23.01.2026 16:00-17:15 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 26.01.2026 12:30-17:30 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 27.01.2026 15:00-16:45 -1947, Studentenarb. m. DV , Support for programming assignments (not mandatory)
- 27.01.2026 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 29.01.2026 10:00-14:00 Z921, Studentenarbeitsraum m. DV , Support for programming assignments (not mandatory)
- 29.01.2026 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
- 03.02.2026 16:45-18:15 N 1189, Hans-Piloty-Hörsaal
- 05.02.2026 16:45-18:15 N 1179, Wilhelm-Nusselt-Hörsaal
Admission information
Objectives
The students shall be able to design a secure embedded system. In particular, to implement given tasks on an embedded system and to assess and choose appropriate measures to secure an embedded system. The former includes being able to
- Use toolchains for embedded development
- Discuss memory organisation
- Classify types of on-chip memory
- Recall the boot process of a uC
- Describe and use memory mapped I/O
- List common peripherals and explain their purpose
- Explain and use interrupts
- Compare and use methods for embedded debugging
while the latter encompasses the ability to
- List security objectives
- Exemplify typical vulnerabilities
- Apply some common attacks
- Choose appropriate countermeasures
- Use cryptography
- Illustrate methods for separation
- Explain and use MMUs/MPUs
- Explain side channels
- Demonstrate the concept of trusted computing
- Use toolchains for embedded development
- Discuss memory organisation
- Classify types of on-chip memory
- Recall the boot process of a uC
- Describe and use memory mapped I/O
- List common peripherals and explain their purpose
- Explain and use interrupts
- Compare and use methods for embedded debugging
while the latter encompasses the ability to
- List security objectives
- Exemplify typical vulnerabilities
- Apply some common attacks
- Choose appropriate countermeasures
- Use cryptography
- Illustrate methods for separation
- Explain and use MMUs/MPUs
- Explain side channels
- Demonstrate the concept of trusted computing
Description
To enable students to implement given tasks on an embedded system, the course will deal with:
- Introduction to microcontrollers, differences to desktop computers
- Memory in embedded systems and its usage by C compilers
- Typical peripherals and their usage
- Interrupts and exceptions
- Embedded debugging
The ability to assess and choose appropriate measures to secure embedded systems motivates:
- Short introduction to security objective and cryptographic operations
- Typical vulnerabilities in embedded systems
- Common attacks and countermeasures
- A note on side-channels
- Concepts of separation and trusted computing
- Introduction to microcontrollers, differences to desktop computers
- Memory in embedded systems and its usage by C compilers
- Typical peripherals and their usage
- Interrupts and exceptions
- Embedded debugging
The ability to assess and choose appropriate measures to secure embedded systems motivates:
- Short introduction to security objective and cryptographic operations
- Typical vulnerabilities in embedded systems
- Common attacks and countermeasures
- A note on side-channels
- Concepts of separation and trusted computing
Prerequisites
C programming
Basic knowledge in computer architectures
Basic knowledge in computer architectures
Teaching and learning methods
Knowledge will be taught using slides and notes on the blackboard. Learning by students is supported within the exercises through interactive problem discussion, group work and live programming. Programming exercises during the semester give students the opportunity to train and show their skills on real hardware.
Examination
The above mentioned abilities of discussing, classifying, recalling, describing, listing, explaining, comparing, exemplifying, choosing, illustrating, and demonstrating will be assessed by answering open questions, analyzing code examples and calculating problems in a written exam making up 80% of the final grade. The abilities of using and applying are assessed through programming exercises during the course, which make up the remaining 20% of the final grade.
Recommended literature
The definitive guide to ARM Cortex-M3 and Cortex-M4 processors
Joseph Yiu
Understanding Cryptography
Christoph Paar, Jan Pelzl
Accompanied lecture slides: http://www.crypto-textbook.com
Handbook of Applied Cryptography
Alfred J. Menezes, Paul C. van Oorschot, Scott A. Vanstone
Download from: http://www.cacr.math.uwaterloo.ca/hac/
Security Engineering
Ross Anderson
Download from: https://www.cl.cam.ac.uk/~rja14/book.html
Joseph Yiu
Understanding Cryptography
Christoph Paar, Jan Pelzl
Accompanied lecture slides: http://www.crypto-textbook.com
Handbook of Applied Cryptography
Alfred J. Menezes, Paul C. van Oorschot, Scott A. Vanstone
Download from: http://www.cacr.math.uwaterloo.ca/hac/
Security Engineering
Ross Anderson
Download from: https://www.cl.cam.ac.uk/~rja14/book.html
Links
Important and additional Information
An additional lab is part of this module.
Offered in winter and summer semester.
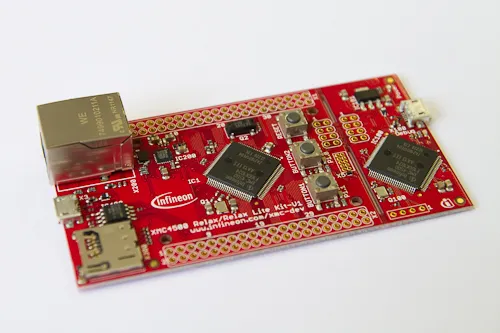
Programming exercises on an embedded system by Infineon will give the opportunity to apply the knowledge acquired in the lectures.
Moodle
Slides will be uploaded to the lecture's Moodle Course after each session.
Language
English (winter semester), German (summer semester)
Marble Run
In the Embedded Systems and Security exercise, the students program a remote control for the marble run in the video on their Infineon XMC4500 Relax Lite board. The marble run ist started in case of a successfull authentication.
As an alternative, the marble run can be started by breaking a 16 bit mini RSA encryption.
It can be accessed unter http://10.152.249.7/ (only from inside the TUM network)