Invasive Attacks
Contact: Michael Weiner
Hardware attacks that require physical manipulations on semiconductors are called invasive. In comparison to non-invasive and semi-invasive attacks, they are the most powerful attack class, but also the most expensive one.
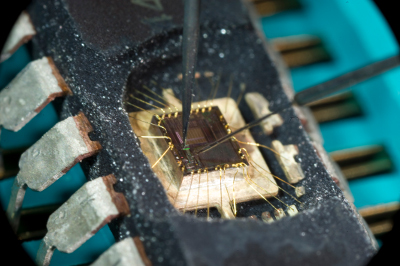
One well-known invasive attack is called microprobing. Microprobing means attaching microscopic needles onto the internal wiring of a chip; this can be used to either read out internal secrets that are not intended to leave the chip, or it can be used for fault attacks.
On the electrical side, attaching a probe acts as connecting a capacitor in the femtofarad range to the attacked line. In a more simplified model, the attacked line gets slower. This can be measured in order to detect microprobing.
While the equipment required for microprobing - microscope, micropositioners, probes, amplifiers - may sound expensive, the second-hand market makes all attack equipment available even for individuals. This makes it important to research on low-cost protection mechanisms.
Research Topics
- low-area microprobing detection circuits
- concepts to detect other invasive attacks such as backside polishing
- stability evaluation and improvement of detection circuits
Selected Publications
Michael Weiner, Salvador Manich and Georg Sigl, A Low Area Probing Detector for Power Efficient Security ICs, Workshop on RFID Security (RFIDsec), Springer, July 2014.
Michael Weiner, Salvador Manich and Georg Sigl, A Low Area Probing Detector for Security ICs, TRUDEVICE Workshop Test and Fault Tolerance for Secure Devices, May 2014.
Salvador Manich, Markus Wamser and Georg Sigl, Detection of probing attempts in secure ICs, Symposium on Hardware-Oriented Security and Trust (HOST), IEEE, June 2012.