SmartCard Lab
| Lecturer (assistant) | |
|---|---|
| Number | 0000000507 |
| Type | |
| Duration | 4 SWS |
| Term | Sommersemester 2024 |
| Language of instruction | German |
| Position within curricula | See TUMonline |
| Dates | See TUMonline |
Admission information
Note: Die Teilnahme an der Einführungsveranstaltung ist verpflichtend.
Objectives
Description
Prerequisites
Teaching and learning methods
Examination
Recommended literature
Links
Additional Information
Offered in winter and summer semester.
Course
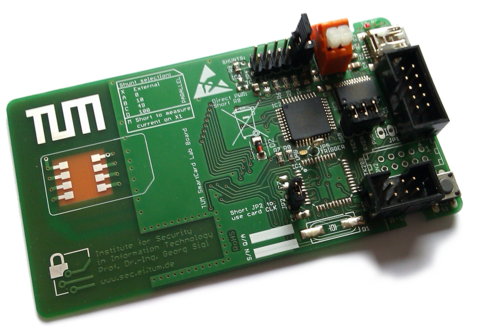
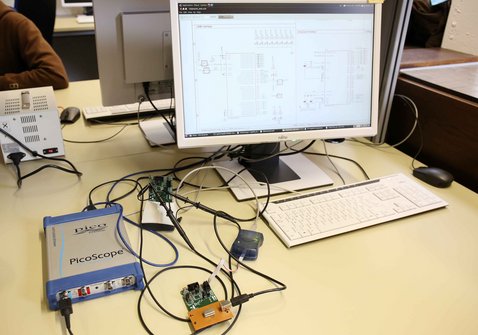
During the course of this lab, students learn how attacks on the implementation of cryptographic algorithms (so-called Side-Channel Attacks) work, and learn to implement countermeasures that help thwart these attacks. Students work in groups of 2-3 people. <br/> The attacks are carried out with high-precision, high-resolution oscilloscopes. The data measurements are then processed with Matlab on a PC. The cryptographic algorithms with the attack countermeasures are implemented on 8-bit microcontrollers, which can be accessed via a standard interface with a smartcard reader (ISO 7816 UART).
Introduction to the Lab: Introduction to the lab tasks, and presentation of attack scenarios
Introduction to DPA (Differential Power Analysis): Overview of the AES algorithm, attacks on the implementation of AES and demonstration.
Integration phase:
Creation of a clone card by using a key extracted by performing attacks on the reference card.
- Work distribution:
- Team A: Differential Power Analysis (DPA) attack, extraction of cryptographic keys, and documentation
- Team B: Design of a Smartcard based on a microcontroller, creation of a test environment, implementation of the ISO7816 protocol
Presentation of intermediate results
Introduction of countermeasures:
- Work distribution:
- Team A: Implementation of attack countermeasures
- Team B: DPA attacks on the new card, and evaluation of the countermeasures
Final presentation
Please find above the scheduled dates for the lectures and presentations.
Contact: Michael Gruber, m.gruber@tum.de