Memory-Protected and Cyber-Resilient Embedded Devices for Internet of Things (IoT) and Cyber-Physical Systems (CPS)
Contact: Jens Nöpel, Utku Budak
The Internet of Things (IoT) is an emerging computing paradigm in which heterogeneous smart devices and appliances are interconnected via IP-based networks to enable data collection, automation, and remote interaction across diverse use cases such as smart homes and wearables. These devices often rely on highly resource-constrained embedded platforms tailored for specific tasks, yet they are expected to operate reliably in dynamic and untrusted environments. On the other hand, Cyber-Physical Systems (CPS) tightly integrate computation and networking with physical processes. As a result, CPS must fulfill stringent requirements for safety, reliability, and availability, placing strong demands on robust SoC-level security and fault-tolerant architectural support to preserve operational integrity. Representative CPS include industrial control systems used in manufacturing plants, power generation facilities, and water treatment infrastructures. Although these systems were traditionally deployed within isolated, proprietary networks, they are increasingly adopting open communication technologies, evolving into networked CPS that make them prone to remote attacks. Furthermore, as the hardware and software stack in such systems grows more complex to support advanced functionality, the corresponding attack surface also expands.
Successful attacks on IoT devices or CPS have far-reaching consequences because they affect not only digital components but also the physical processes they control. Tampering with sensor readings, control logic, or actuator signals can induce system malfunctions, disrupt operations, or create serious safety hazards. Therefore, ensuring their resilience, the ability to sustain secure and correct operation under faults, adversarial actions, or abnormal conditions, has become an essential aspect while designing these systems. To address these challenges, modern embedded platforms integrate various mechanisms such as memory encryption, integrity-protected storage hierarchies, integrity verification, and error-correcting codes (ECC) to safeguard data, code, and execution against tampering or corruption. With further complementary resilience features, such as fault-injection resistance, redundant execution, and runtime anomaly detection, they aim to ensure continuous, predictable operation even under attack. These mechanism are often enabled or strengthened by hardware-based security architectures such as Trusted Execution Environments (TEEs), memory-protection technologies, Trusted Platform Modules (TPMs), Device Identifier Composition Engine (DICE) or other solutions. Together, these mechanisms establish a trusted foundation that enhances the confidentiality, integrity, and operational reliability of IoT and CPS platforms deployed in increasingly hostile and interconnected environments.
The research in our institute brings together different aspects of security:
- Secure implementation of embedded hardware/software with respect of side channel analysis
- Tools to support developers in designing secure systems
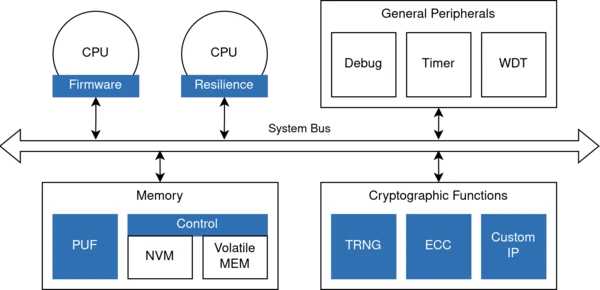
- Integration of standard hardware security modules into embedded systems
- Architectures for secure hardware/software systems
- Resilient system- and SoC-level designs to ensure dependable operation under faults and adversarial conditions
- Hardware-assisted memory protection mechanisms, including memory encryption, integrity verification, and error-correction (ECC)
- Secure boot, key management, and hardware-rooted trust anchors for embedded and cyber-physical systems
Selected Publications
2025
J. Nöpel, T. Music, N. Stein, C. Frisch and M. Pehl, "Quantization Schemes for PUFs: The Entropy-Area Trade-Off," 2025 IEEE International Symposium on Hardware Oriented Security and Trust (HOST), San Jose, CA, USA, 2025, pp. 289-299, doi: 10.1109/HOST64725.2025.11050043.
U. Budak, F. D. Santis, O. Yasar, M. Safieh and G. Sigl, "A Lightweight Firmware Resilience Engine for Real-Time Operating Systems," 2025 IEEE International Conference on Cyber Security and Resilience (CSR), Chania, Crete, Greece, 2025, pp. 401-406, doi: 10.1109/CSR64739.2025.11129996.
Budak, U., Safieh, M., De Santis, F., Sigl, G. (2025). A Cyber-Resilient DICE Architecture for Resource-Constrained Devices. In: Skopik, F., Naessens, V., De Sutter, B. (eds) Availability, Reliability and Security. ARES 2025. Lecture Notes in Computer Science, vol 15998. Springer, Cham. doi.org/10.1007/978-3-032-00642-4_5
2024
U. Budak, F. D. Santis and G. Sigl, "A Lightweight Firmware Resilience Engine for IoT Devices Leveraging Minimal Processor Features," 2024 IEEE International Conference on Cyber Security and Resilience (CSR), London, United Kingdom, 2024, pp. 486-491, doi: 10.1109/CSR61664.2024.10679408. (Best Paper Award)
J. Schupp, P. Karl, J. Nöpel, A. Hepp, T. Music and G. Sigl, "RISC-V Triplet: Tapeouts for Security Applications," 2024 IEEE Nordic Circuits and Systems Conference (NorCAS), Lund, Sweden, 2024, pp. 1-6, doi: 10.1109/NorCAS64408.2024.10752453.