Da wir uns an ein internationales Publikum richten, ist diese Webseite nur auf Englisch verfügbar.
Cyber Physical Systems
Professorship in Heilbronn
Our research stands at the crossroads of guaranteeing safety and privacy in cyber-physical systems. We aim to guarantee the safe usage of reinforcement learning and large language models in robotics. With a focus on data-driven reachability analysis, we delve into the intricate task of ensuring the safety of cyber-physical systems. Leveraging advanced computational techniques, we explore how reachability analysis can proactively identify potential hazards and ensure that cyber-physical systems operate within predefined safety boundaries. Simultaneously, we address the critical issue of privacy in an age where data is abundant and incredibly sensitive. By harnessing the power of homomorphic encryption, our research tackles the formidable challenge of preserving the confidentiality of data while still allowing for meaningful computation. This encryption paradigm enables computations to be performed on encrypted data without the need for decryption, thereby creating a safeguard against unauthorized access to sensitive information.
People
Professor

Professor for Cyber Physical Systems
Email: alanwar[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.16
Secretary

+49 (0)7131 26418903
man.kiessling-lyu[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.4.05
Scientific Researchers

Ahmad Hafez; M.Sc., M.Sc.
a.hafez[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.17

Peng Xie; M.Sc.
p.xie[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.17

Zhen Zhang; M.Eng.
zhenzhang.zhang[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.17

Hesham Mousa; M.Sc.
hesham.mousa[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.17

Wenyuan Wu; M.Sc.
wenyuan.wu[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.17

Yanliang Huang; M.Sc.
yanliang.huang[at]tum[dot]de
Office: Bildungscampus 2, 74076 Heilbronn, Room D.3.17
Master’s Thesis Opportunity
Adaptive Computation For LLMs through Nested Model Architectures
Teaching
Winter Semester Courses
Summer Semester Courses
Research
Safe LLM-Controlled Robots

Our work investigates the problem of instructing a Large Language Model (LLM) to navigate the vehicle to a specified goal and assesses its ability to generate low-level control actions that successfully guide the robot safely toward that goal. By leveraging historical data to construct reachable sets of states for the vehicle, our approach provides rigorous safety guarantees against unsafe behaviors without relying on explicit analytical models. This work advances the integration of formal methods into LLM-based robotics, offering a principled and practical approach to ensuring safety in next-generation autonomous systems.
Reference: Safe LLM-Controlled Robots with Formal Guarantees via Reachability Analysis
Videos: Video 1
Data Driven Reachability Analysis
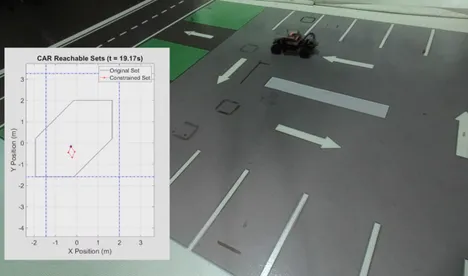
Reachability analysis computes the set of reachable states of a model with uncertain initial states, inputs, and parameters. One major application of reachability analysis is the formal verification and controller synthesis of CPS. Most current reachability analysis heavily relies on the existence of a suitable system model, which is often not directly available in practice as systems are becoming more sophisticated. One often has an abundance of data but no model to perform reachability analysis. It is sometimes even easier to learn control policies directly from data rather than learning a model. Therefore, we aim to propose reachability analysis using data-driven approaches.
Reference: Data-Driven Reachability Analysis from Noisy Data
Safety Guaranteed Reinforcement Learning

Reinforcement learning is capable of creating sophisticated controllers in uncertain environments. However, state-of-the-art reinforcement learning approaches lack safety guarantees, especially when the robot’s model and surrounding moving objects’ models are unknown. It is essential to ensure reasonable system performance and respect safety constraints during the process of learning policies that maximize the expectation and during deployment processes of reinforcement learning. We address this challenge by augmenting reinforcement learning with a safety layer that is based on formal data-driven verification techniques.
Reference: Safe Reinforcement Learning Using Black-Box Reachability Analysis
Videos: Video 1
Application of Logical Zonotopes
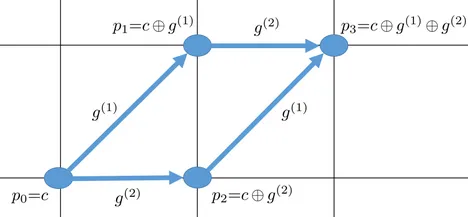
A logical zonotope is constructed by XORing a binary point vector with a combination of binary vectors called generators. It can efficiently represent up to 2^n binary states of a logic-based system using only n generators. This can reduce the complexity of many exhaustive search algorithms by performing logical operations over the generators instead of iterating over the original binary vectors. Logical zonotopes are closed under XOR and NOT operations and yield over-approximations under AND and NAND operations. Since NAND is a universal gate operation, under the remaining operations, OR, NOR, and XNOR, logical zonotopes also yield over-approximations.
Reference: Logical Zonotope: A Set Representation for Binary Vectors
Privacy-Preserving Set-Based Estimation using Homomorphic Encryption

We work on set-based estimation using partially homomorphic encryption that preserve the privacy of the measurements and sets bounding the estimates. We establish the notion of encrypted sets and intersect sets in the encrypted domain, which enables guaranteed state estimation while ensuring privacy. In particular, we show that our protocols achieve computational privacy by using the cryptographic notion of computational indistinguishability.
Reference: Privacy Preserving Set-Based Estimation Using Partially Homomorphic Encryption
Shared Situational Awareness with V2X Communication

The ability to perceive and comprehend a traffic situation and to predict the intent of vehicles and road-users in the surrounding of the ego-vehicle is known as situational awareness. We work on a framework to improve situational awareness using set-membership estimation and vehicle-to-everything (V2X) communication. This framework provides safety guarantees and can adapt to dynamically changing scenarios, and is integrated into an existing complex autonomous platform.
Selected Publications
- Ahmad Hafez, Alireza Naderi Akhormeh, Amr Hegazy, Amr Alanwar “Safe LLM-Controlled Robots with Formal Guarantees via Reachability Analysis” (link)
- Mahmoud Selim, Amr Alanwar, Shreyas Kousik, Grace Gao, Marco Pavone, Karl H Johansson "Safe Reinforcement Learning Using Black-Box Reachability Analysis". IEEE Robotics and Automation Letters (link)
- Amr Alanwar, Frank J Jiang, Maryam Sharifi, Dimos V Dimarogonas, Karl H Johansson "Enhancing Data-Driven Reachability Analysis using Temporal Logic Side Information" International Conference on Robotics and Automation (ICRA 2022) (link)
- Amr Alanwar, Alexndder Berndt, Karl Henrik Johansson, Henrik Sandberg, Data-driven set-based estimation using matrix zonotopes with set containment guarantees, 20th European Control Conference (ECC 2022) (link)
- Vandana Narri, Amr Alanwar, Jonas Mårtensson, Christoffer Norén, Laura Dal Col, Karl Henrik Johansson "Set-Membership Estimation in Shared Situational Awareness for Automated Vehicles in Occluded Scenarios", IEEE Intelligent Vehicles Symposium (link)
- Sawsan Emad, Amr Alanwar, Yousra Alkabani, M Watheq El-Kharashi, Henrik Sandberg, Karl H Johansson "Privacy Guarantees for Cloud-based State Estimation using Partially Homomorphic Encryption" European Control Conference (ECC 2022) (link)
- Amr Alanwar, Muhammad Umar B Niazi, Karl H Johansson "Data-driven Set-based Estimation of Polynomial Systems with Application to SIR Epidemics" European Control Conference (ECC 2022) (link)
- Amr Alanwar, Yvonne Stürz, Karl Henrik Johansson "Robust data-driven predictive control using reachability analysis" European Journal of Control (link)
- Amr Alanwar, and Anne Koch, Frank Allgöwer, Karl Henrik Johansson "Data-Driven Reachability Analysis from Noisy Data" IEEE Transactions on Automatic Control (link)
- Amr Alanwar, and Anne Koch, Frank Allgöwer, Karl Henrik Johansson "Data-Driven Reachability Analysis Using Matrix Zonotopes" Annual Learning for Dynamics & Control Conference (L4DC 2021) (link)
- Amr Alanwar, Victor Gassmann, Xingkang He, Hazem Said, Henrik Sandberg, Karl Henrik Johansson, Matthias Althoff "Privacy Preserving Set-Based Estimation Using Partially Homomorphic Encryption" European Journal of Control (link)
- Amr Alanwar, Hazem Said, Ankur Mehta, Matthias Althoff "Event-Triggered Diffusion Kalman Filters" 11th ACM/IEE International Conference on Cyber-Physical Systems (ICCPS),2020. (acceptance rate 24/101 = 23.7%). (link)
- Amr Alanwar, Jagat Jyoti Rath, Hazem Said, Karl Henrik Johansson, Matthias Althoff "Distributed Set-Based Observers Using Diffusion Strategy" Journal of the Franklin Institute (link).
- Amr Alanwar, Bharathan Balaji, Yuan Tian, Shuo Yang, Mani Srivastava "EchoSafe: Sonar-based Verifiable Interaction with Intelligent Digital Agents". SafeThings ACM Workshop on the Internet of Safe Thing, 2017 (ACM SafeThings). (link)
- Amr Alanwar, Henrique Ferraz, Kevin Hsieh, Rohit Thazhath, Paul D. Martin, Joao Hespanha, and Mani B. Srivastava "DSLATS: Distributed Simultaneous Localization and Time Synchronization" Proceedings of the 18th ACM international symposium on Mobile Ad Hoc networking and computing, July 2017 (ACM MobiHoc). (Acceptance rate=15%) (Video) (link)
- Amr Alanwar, Yasser Shoukry, Supriyo Chakraborty, Paul D. Martin, Paulo Tabuada, and Mani B. Srivastava. PrOLoc: Resilient Localization with Private Observers Using Partial Homomorphic Encryption. ACM/IEEE International Conference on Information Processing in Sensor Networks, April 2017 (ACM/IEEE IPSN). (Acceptance rate=18%) (link)
- Amr Alanwar, Yasser Shoukry, Supriyo Chakraborty, Paul D. Martin, Paulo Tabuada, and Mani B. Srivastava. Demo abstract: PrOLoc: Resilient Localization with Private Observers Using Partial Homomorphic Encryption. ACM/IEEE International Conference on Information Processing in Sensor Networks, April 2017 (ACM/IEEE IPSN). (Best Demonstration paper Award) (link)
- Amr Alanwar, Moustafa Alzantot, Bo-Jhang Ho, Paul D. Martin, and Mani B. Srivastava. "SeleCon: Scalable IoT Device Selection and Control Using Hand Gestures" Second International Conference on Internet-of Things Design and Implementation, April 2017. (ACM/IEEE IoTDI). (Acceptance rate=29%) (link)
- Amr Alanwar, Fatima M Anwar, Yi-Fan Zhang, Justin Pearson, Joao Hespanha, Mani B Srivastava. "Cyclops: PRU Programming Framework for Precise Timing Application" In Proceedings of the International IEEE Symposium on Precision Clock Synchronization for Measurement, Control, and Communication (IEEE ISPCS 2017) (link) (Video)
- Henrique Ferraz, Amr Alanwar, Mani Srivastava, Joao P Hespanha. Node Localization Based on Distributed Constrained Optimization using Jacobi’s Method 56th IEEE Conference on Decision and Control 2017 (IEEE CDC) (link)
- M. T. I. Ziad, Amr Alanwar, Moustafa Alzantot, Mani Srivastava. "CryptoImg: Privacy Preserving Processing Over Encrypted Images". 2016 IEEE Conference on Communications and Network Security (IEEE CNS). (link)
- Yasser Shoukry, Konstantinos Gatsis, Amr Alanwar, George J. Pappas, Sanjit A. Seshia, Mani Srivastava, Paulo Tabuada."Privacy-Aware Quadratic Optimization Using Partially Homomorphic Encryption". IEEE 55th Conference on Decision and Control 2016 (IEEE CDC). (link)
- M. T. I. Ziad, Amr Alanwar, Yousra Alkabani, M. Watheq El-Kharashi, Hassan Bedour, "Homomorphic Data Isolation for Hardware Trojan Protection", Proc. of the IEEE Computer Society Annual Symposium on VLSI 2015 (IEEE ISVLSI). (link)